Assigning Windows 10/11 Enterprise Subscription Activation Licences to Hybrid Azure AD Joined Devices
Introduction
Starting with Windows 10, version 1703, Windows 10 Pro supports the Subscription Activation feature, enabling users to “step-up” from Windows 10 Pro to Windows 10 Enterprise automatically if they are subscribed to Windows 10 Enterprise E3 or E5.
The Subscription Activation feature eliminates the need to manually deploy Windows 10 Enterprise or Education images on each target device, then later standing up on-prem key management services such as KMS or MAK based activation, entering GVLKs, and subsequently rebooting client devices.
It’s important to note that the Windows 10 Enterprise subscription activation is designed to “step-up” a device from Windows 10 Pro to Windows 10 Enterprise. Therefore, your device is required to have a Windows 10 Pro license activated as a baseline.
For Windows 10 Enterprise Subscription Activation to function, there a several prerequisites which need to be in place. This blog is aimed for organisations which have Active Directory on premises and synchronise their AD objects to Azure AD via AD Connect.
Overall Prerequisites
The below provide a summary breakdown of the prerequisites required in the setup on AAD Connect:
- AAD Connect | Setup Check/Update
- AAD Connect | Hybrid Azure AD Join
- AAD Connect | Review/Amend OU Sync Scope
- Client Device | Internet Access to Azure AD via SYSTEM Account
- Client Device | Internet Access to Azure AD via User Account
- Client Device | SSO IE Local Intranet Settings
- Client Device | Windows 10 Pro Licensed and Activated
- Azure AD | Valid Subscription Present
- Azure AD | Applicable Users Licensed with Windows 10 Enterprise
AAD Connect | Setup Check/Update
- Version of 1.1.819.0 or above (you need to be v2 now anyway)
- Hybrid Azure Active Directory Join enabled and configured
- Sync scope to include the OU’s which contain the applicable computer objects
AAD Connect | Hybrid Azure AD Join
Below is an example of the where the SCP shows in Active
Directory:
AAD Connect | Review/Amend OU Sync Scope
Client Device
- Internet Access to Azure AD via SYSTEM account
- Internet Access to Azure AD via User Account
- SSO IE Local Intranet Settings
- Device licensed and activated with Windows 10 Pro
Client Device | Internet Access to Azure AD via SYSTEM Account
- https://enterpriseregistration.windows.net
- https://login.microsoftonline.com
- https://device.login.microsoftonline.com
- https://autologon.microsoftazuread-sso.com
- Your ADFS server address if you have one e.g. https://sts.company.com
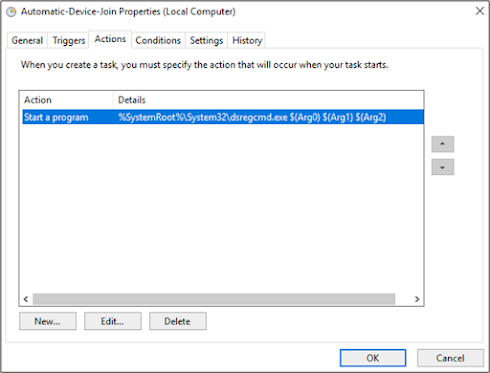
Automatic Device Join Scheduled Task
userCertificate Attribute
AAD Connect Device Sync Rule Filter
Test Azure AD Connection for SYSTEM account
Manually setting proxy for SYSTEM account
Azure AD Hybrid Azure AD Join status
Client Device | Internet Access to Azure AD via User Account
Client Device | SSO IE Local Intranet Settings
In order to provide Seamless SSO for the license subscription to works silently, the following URL’s should be added into the users Local Intranet zone in Internet Explorer:
- https://device.login.microsoftonline.com
- https://autologon.microsoftazuread-sso.com
Push Out Settings via Group Policy
You can push out the Local Intranet Settings to users via a
Group Policy. Below is an example of the
settings which need to be configured under the user context:
Client Device | Windows 10 Pro Licensed and Activated
For the step-up in license from Windows 10 Pro to Enterprise
to occur, you’re required to have your device licensed and activated with
Windows 10 Pro as a foundation.
Note, Windows 10, version 1803 enables pulling activation keys directly from firmware where the device support firmware-embedded keys. It is no longer necessary to run a script to perform the activation step on Windows 10 Pro prior to activating Enterprise.
Windows Edition Check
Below is an example of how the Windows 10 Pro license should display prior to step-up in license. Disregard the partial product key as this may be different prior to the step-up in licensing:
Azure AD
- An applicable license plan in the Azure AD/Office 365 tenant
- A license assigned to the applicable users for the step-up in licensing
Azure AD | Valid Subscription Present
Azure AD | Applicable Users Licensed with Windows 10 Enterprise
Enable Licence Subscription
Windows 10 Subscription Activation
- Note, in some places the license will still appears as Windows 10 Pro.
- Note, that the partial product key should show with the value 3V66T.
- Note, a user can license up to 5 devices with their user account. The activation is like a queue, the 1st activated device will drop off the list when a 6th one is activated etc.
- At the present time, there’s no documented way to verify which and how many devices have been licensed by user account in Azure AD.
- Upon revoking the license from the user in Azure AD/Office 365, the license will downgrade back to Windows 10 Pro.







































Hi, great article, followed all steps. We have in the company, that we lose activation. are you familiar with such cases? who can trigger. we have CA, we excluded a lot of services that it would not cause but we are still downgrading license from Ent to Pro.
ReplyDeleteWhenever I have seen this, it's usually due to the user no longer having a Windows 10/11 Ent license assigned.
Deletelicense exist, i am sure, we are losing randomly, and it is massive way now.
DeleteVery hard to say what the issue is without more detail. What have checked? I would recommned looking at items from Rudy in his site too - https://call4cloud.nl/2022/02/escape-from-windows-10-pro/
DeleteGreat article. We are looking at doing just this. Upgrading our Win10 pros to 11 enterprise. I assume this is still relevant and current in Jan23?
ReplyDeleteI presume if we aren't using the device options in ADC and we already have some devices showing in AAD then ADC will upgrade/replace these computer objects? The existing objects in AAD are devices that have registered Outlook app, Teams clients and Office i believe.
My concern is that of duplicate computer IDs or replacement IDs which in turn could affect existing users/computers?
Thanks
Yes, this still should be relevant. As a note, a colleague of mine (https://www.linkedin.com/in/russellwbmckee/) came across an issue where HAADJ some devices conflicted with an already registered Azure AD Registered device; but they were in the minority. However, as I understand, this should typically be taken care of, where the Azure AD Registered device and HAADJ become merged.
DeleteIn cases where that merge doesn't happen, there may be a need for you to to disconnect/leave the tenant via Work/School account on the Windows devices in order to get the HAADJ process to work.
Please feedback and let us know how you got on and what you discover in your setup.
Interestingly we see the our .local domain under the SCP value and not sure how to proceed.
DeleteGot there in the end. All synching and showing in Intune. Thanks again
DeleteSuperb, glad you got there. Did you hit any snags or issues that weren't in the above?
DeleteNo, it worked fine
Delete